A brute force attack is a trial-and-error technique used to guess the credentials and log into a system. However, Microsoft has now added a Group Policy to all Windows versions named “Allow Administrator account lockout,” which is an account lockout policy applicable to the local Administrator account. Previously, this policy was only available for Windows 11. However, now, this is available for all versions, including Windows 10. Furthermore, now, this policy is enabled by default. This means, if you have configured the “Account lockout threshold” policy and incorrect credentials are entered in the same amount of time, the account will be locked and the user will be unable to enter more credentials. Let us now discuss the policy in depth and see how to configure it.
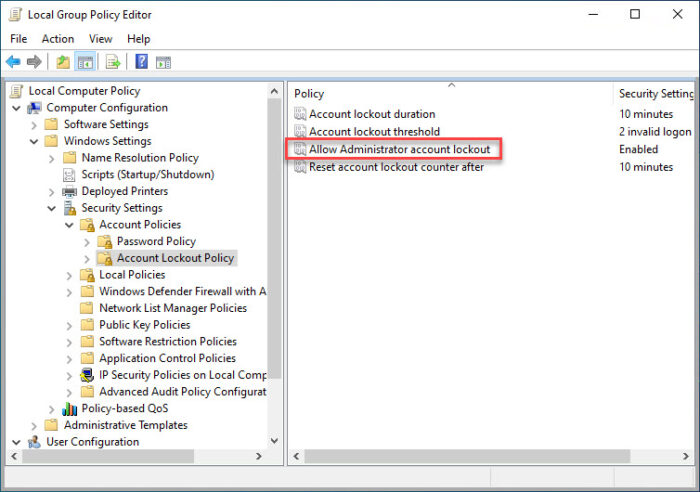
What is “Allow Administrator Account Lockout” GPO
The “Allow Administrator account lockout” policy was earlier added to Windows 11 only but had recently been integrated into other versions as well. By enabling this Group Policy, the local Administrator account (if enabled) will automatically lock for a set period after a set number of failed sign-in attempts within a set amount of time. We use the word “set” because these values are configurable. By default, the Administrator account will lock itself for 10 minutes when the said number of wrong attempts is entered within 10 minutes. However, these values are changeable. The “Allow Administrator account lockout” group policy can be found at the following path inside the Group Policy editor: Let us now show you how to configure this policy to keep your computer safe from brute force attacks and unauthorized remote logins.
How to Configure Administrator Account Lockout Policy in Windows
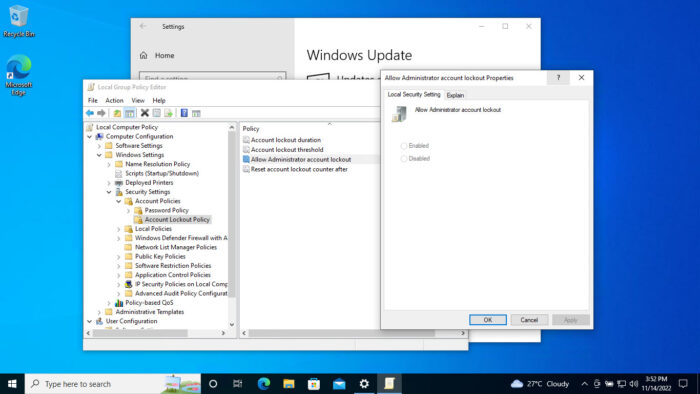
If you go ahead and try to configure the “Allow Administrator account lockout” policy, you will find that the options are grayed out (when no other configuration is done.) This is because this policy is dependent upon the “Account lockout threshold” policy, which needs to be configured first. Its default value is “0,” which means that the account lockout policy is disabled. Moreover, 2 more GPOs work in coherence to form the Administrator account lockout policy. Here are the details for these policies:
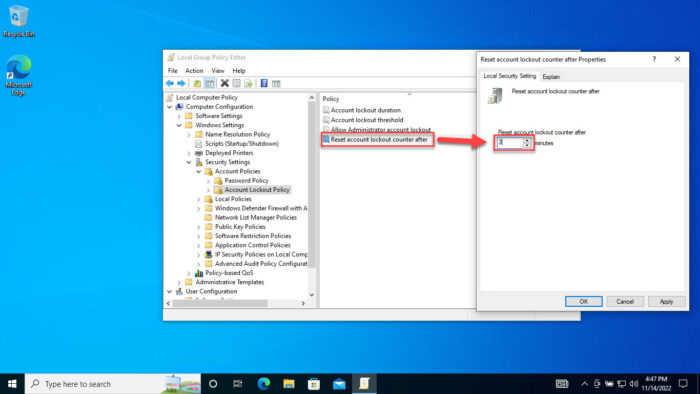
Account lockout duration The time (in minutes) for when the user will be unable to sign back in, even with the correct credentials. Range: 0-99,999 minutes. Account lockout threshold Defines how many tries before the Administrator account is locked and no more login attempts are granted. Range: 0-999 Allow Administrator account lockout Whether the Administrator account will be locked out or not. Reset account lockout counter after Defines the number of minutes that must elapse after a failed logon attempt before the failed logon attempt counter is reset to 0 bad logon attempts. Range: 1-99,999 minutes.
Now that you understand what each of these policies is for, follow these steps to configure your local Administrator account to lockout: The time (in minutes) for when the user will be unable to sign back in, even with the correct credentials. Range: 0-99,999 minutes. Defines how many tries before the Administrator account is locked and no more login attempts are granted. Range: 0-999 Whether the Administrator account will be locked out or not. Defines the number of minutes that must elapse after a failed logon attempt before the failed logon attempt counter is reset to 0 bad logon attempts. Range: 1-99,999 minutes. Your local Administrator account will now automatically lock itself and deny any login attempts when incorrect login attempts are made that satisfy your policy configurations. Click Apply and Ok when done. Note: If you do not want the Administrator account to lock out but want only the other accounts, then set this policy to Disabled. Click Apply and Ok when done. Note: This value should be less than or equal to the value for “Account lockout duration.” Click Apply and Ok when done. If you want to disable this feature in the future, all you need to do is change the value for “Account lockout threshold” to 0, and all other policies will return to their default values automatically.
Final Analysis
Having an added layer of security is always beneficial. By configuring the local Administrator account to lockout, you keep an intruder from entering the computer account with the most elevated privileges. Even if an attacker were to succeed and eventually enter the correct password, it would now take them much longer to achieve that goal, since the account will be locked out for several minutes. Also see:
2 ways to reset Local Group Policy in Windows 10 3 Ways To Remove/Disable Microsoft Account In Windows 11/10 Enable, Disable Or Delete Built-In Administrator Account In Windows 10 How to Create Administrator Account in Windows 10 3 Ways To Set Windows Local User Account Passwords To Never Expire